Zero-Knowledge Proofs: Crypto’s Privacy Guardian
We live in a digital age where data is the new gold. But with this increased reliance on digital information comes an inherent risk: privacy breaches. The more we share online, the more vulnerable we become. Thankfully, the world of cryptography offers a powerful solution: Zero-Knowledge Proofs (ZKPs).
Think of ZKPs as the ultimate magic trick. You get to prove you possess certain information without actually revealing the information itself. Sounds impossible? That’s the beauty of it!
Imagine trying to enter a bar that requires you to be over 21. Traditionally, you’d show your ID, revealing personal details beyond just your age. With a ZKP, you could prove you’re of age without divulging your birthdate, address, or even your name.
Intrigued? Let’s dive deeper into this fascinating cryptographic innovation.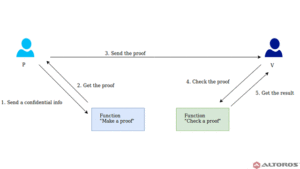
Unmasking the Power: Security Without Compromise
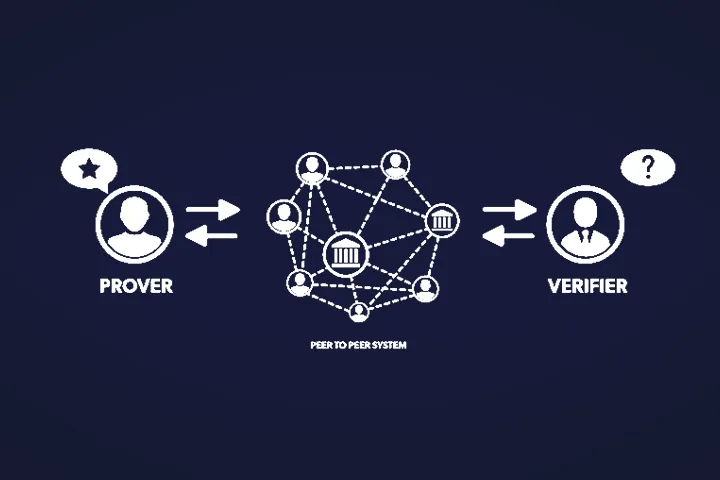
At its core, a Zero-Knowledge Proof involves two parties:
- The Prover: The one claiming to possess certain information.
- The Verifier: The one who needs to be convinced of the Prover’s claim.
The magic happens through a series of interactions or “challenges” that the Verifier presents. The Prover, using their secret information, successfully answers these challenges without ever revealing the information itself.
Let’s illustrate this with a classic example: “Ali Baba’s Cave.”
Imagine a circular cave with two entrances (let’s call them A and B). The Prover wants to convince the Verifier they know the secret password to open a magic door inside the cave, without actually telling them the password.
Here’s how it works:
- The Setup: The Verifier waits outside while the Prover enters the cave and chooses one of the two entrances (A or B).
- The Challenge: The Verifier shouts out either “A” or “B,” instructing the Prover to appear from that entrance.
- The Response: If the Prover truly knows the password, they can easily open the magic door and exit from the designated entrance.
- Repeat: They repeat steps 1-3 multiple times. With each successful round, the Verifier’s confidence grows that the Prover indeed possesses the secret password.
Notice how the Prover never reveals the actual password but still manages to convince the Verifier of their knowledge. That’s the essence of a Zero-Knowledge Proof!
The Real-World Impact of ZKPs
ZKPs aren’t just theoretical concepts; they’re transforming various sectors:
- Enhanced Blockchain Privacy: ZKPs can mask transaction details on public blockchains, offering anonymity without compromising security. This is particularly crucial for privacy coins like Zcash.
- Secure Identity Verification: Imagine logging into websites or verifying your identity without revealing sensitive personal data. ZKPs can make this a reality.
- Data Integrity Assurance: Companies can use ZKPs to prove they possess certain data sets without revealing the actual data, ensuring both transparency and confidentiality.
- Supply Chain Transparency: ZKPs can track the journey of products through the supply chain, verifying authenticity and ethical sourcing without exposing proprietary information.
Navigating the Challenges
While incredibly promising, ZKPs are not without their limitations:
- Computational Complexity: Generating and verifying ZKPs can be computationally intensive, posing scalability challenges.
- Proof Size: Some ZKPs can be quite large, potentially hindering efficient storage and transmission.
- Quantum Resistance: The rise of quantum computing poses a potential threat to some ZKP constructions, requiring ongoing research and development of quantum-resistant solutions.
The Future is Private and Secure
Despite these challenges, the future of ZKPs is bright. As research advances and technology matures, we can expect to see:
- More Efficient ZKPs: Innovations are constantly being made to make ZKPs more computationally efficient and scalable.
- Wider Adoption: The increasing need for privacy and security will drive the adoption of ZKP technology across various industries.
- New Use Cases: As the technology evolves, we can anticipate novel and creative applications of ZKPs beyond what we can imagine today.
Zero-Knowledge Proofs are revolutionizing the way we think about privacy and security in the digital age. They offer a powerful way to prove possession of information without revealing the information itself, paving the way for a future where privacy and security coexist harmoniously.
FAQs
- Are Zero-Knowledge Proofs already being used?
Yes, ZKPs are already being implemented in various blockchain projects like Zcash and StarkWare, as well as in other industries for identity verification and data security. - How complex is it to understand and implement ZKPs?
The underlying mathematics behind ZKPs can be complex. However, there are resources and libraries available that simplify the implementation process for developers. - What are the different types of Zero-Knowledge Proofs?
There are various types of ZKPs, including zk-SNARKs, zk-STARKs, and Bulletproofs, each with its own trade-offs in terms of efficiency and security. - Can ZKPs be used for anything besides privacy?
Absolutely! ZKPs have applications in verifiable computing, allowing for the verification of complex computations without revealing the inputs or the process. - What is the future of Zero-Knowledge Proofs?
ZKPs are expected to play a crucial role in building a more private and secure digital future, with ongoing research and development driving further innovation and wider adoption.